2017 Sep New 300-375 Exam Dumps with PDF and VCE Free Updated Today! Following are some new 300-375 Questions:
1.|2017 New 300-375 Exam Dumps (PDF &VCE) 77Q&As Download:
https://www.braindump2go.com/300-375.html
2.|2017 New 300-375 Exam Questions & Answers Download:
https://drive.google.com/drive/folders/0B75b5xYLjSSNR21JWVIyUWFaTWM?usp=sharing
QUESTION 21
After receiving an alert regarding a rogue AP, a network engineer logs into Cisco Prime and looks at the floor map where the AP that detected the rogue is located. The map is synchronized with a mobility services engine that determines the rogue device is actually inside the campus. The engineer determines the rogue to be a security threat and decides to stop it from broadcasting inside the enterprise wireless network. What is the fastest way to disable the rogue?
A. Go to the location the rogue device is indicated to be and disable the power.
B. Create an SSID on WLAN controller resembling the SSID of the rogue to spoof it and disable clients from connecting to it.
C. Classify the rogue as malicious in Cisco Prime.
D. Update the status of the rogue in Cisco Prime to contained.
Answer: C
QUESTION 22
An engineer has determined that the source of an authentication issue is the client laptop.
Which three items must be verified for EAP-TLS authentication? (Choose three.)
A. The client certificate is formatted as X 509 version 3
B. The validate server certificate option is disabled.
C. The client certificate has a valid expiration date.
D. The user account is the same in the certificate.
E. The supplicant is configured correctly.
F. The subject key identifier is configured correctly.
Answer: ADF
QUESTION 23
Which three configuration steps are necessary on the WLC when implementing central web authentication in conjunction with Cisco ISE. (Choose three.)
A. Set P2P Blocking Action to Drop.
B. Enable Security Layer 3 Web Policy.
C. Set NAC state to SNMP NAC.
D. Enable Allow AAA override.
E. Enable Security Layer 2 MAC Filtering.
F. Set NAC state to RADIUS NAC.
Answer: DEF
QUESTION 24
A customer has deployed PEAP authentication with a Novell eDirectory LDAP Server. Which authentication method must be configured on the client to support this deployment?
A. PEAP(EAP-MSCHAPv2)
B. PEAP(EAP-TTLS)
C. PEAP(EAP-GTC)
D. PEAP(EAP-WPA)
Answer: C
QUESTION 25
An engineer is considering an MDM integration with Cisco ISE to assist with security for lost devices. Which two functions of MDM increase security for lost devices that access data from the network? (Choose two.)
A. PIN enforcement
B. Jailbreak/root detection
C. data wipe
D. data encryption
E. data loss prevention
Answer: AC
QUESTION 26
An engineer must change the wireless authentication from WPA2-Personal to WPA2- Enterprise. Which three requirements are necessary? (Choose three.)
A. EAP
B. 802.1x
C. RADIUS
D. per-shared key
E. 802.11u
F. fast secure roaming
G. 802.11i
Answer: ACG
QUESTION 27
Which two considerations must a network engineer have when planning for voice over wireless roaming? (Choose two.)
A. Roaming with only 802.1x authentication requires full reauthentication.
B. Full reauthentication introduces gaps in a voice conversation.
C. Roaming occurs when e phone has seen at least four APs.
D. Roaming occurs when the phone has reached -80 dBs or below.
Answer: AB
QUESTION 28
Refer to the exhibit. What is the 1.1.1.1 IP address?
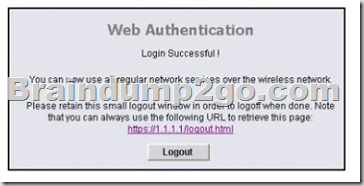
A. the wireless client IP address
B. the RADIUS server IP address
C. the controller management IP address
D. the lightweight IP address
E. the controller AP-manager IP address
F. the controller virtual interface IP address
Answer: F
QUESTION 29
An engineer is deploying EAP-TLS as the authentication mechanism for an 802.1X- enabled wireless network. Which network device is responsible for applying the digital signature to a certificate to ensure that the certificate is trusted and valid?
A. supplicant
B. CA server
C. wireless controller
D. authentication server
Answer: B
QUESTION 30
An engineer is configuring a new mobility anchor for a WLAN on the CLI with the config wlan mobility anchor add 3 10.10.10.10 command, but the command is failing. Which two conditions must be met to be able to enter this command? (Choose two.)
A. The anchor controller IP address must be within the management interface subnet.
B. The anchor controller must be in the same mobility group.
C. The WLAN must be enabled.
D. The mobility group keepalive must be configured.
E. The indicated WLAN ID must be present on the controller.
Answer: AB
!!!RECOMMEND!!!
1.|2017 New 300-375 Exam Dumps (PDF &VCE) 77Q&As Download:
https://www.braindump2go.com/300-375.html
2.|2017 New 300-375 Study Guide Video: