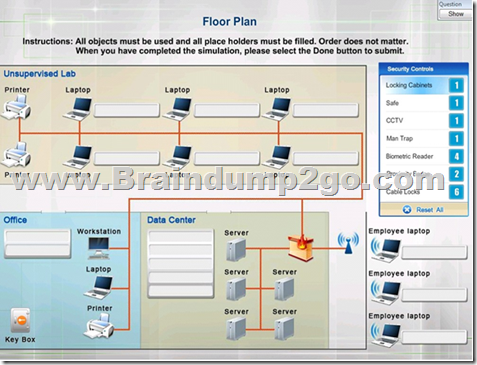
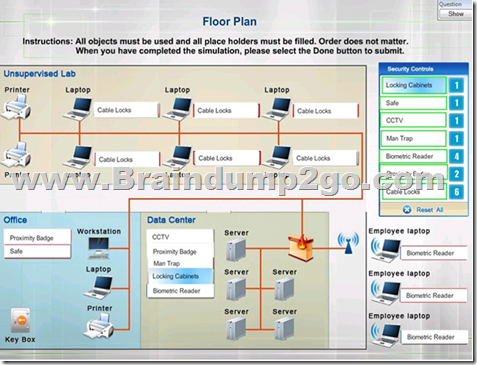
Hello guys, Microsoft 70-534 Exam was Relaced by 70-535 Exam on November 30, 2017. Here we got the latest 70-535 Exam Dumps with PDF and VCE: https://www.braindump2go.com/70-535.html
IMPORTANT: Significant changes are in progress for Exam 534 and its content. We estimate the amount of change to be 30% compared to 534.
As a result, we are retiring 534 on December 31, 2017, and replacing it with Exam 535 that covers the new (but related) objective domain.
Exam 535 retains the same exam title as 534, and 535 will be available in English on November 30, 2017, with other languages following soon after.
You will no longer be able to register for Exam 534 after November 30, 2017. The Online training and Instructor-led training Preparation options below are for Exam 534.
Please use them while we prepare options that are specific to Exam 535.
Detailed 535 Exam info can be see here: https://www.microsoft.com/en-us/learning/exam-70-535.aspx
Following are what you should know about 534 replaced by 535: https://borntolearn.mslearn.net/b/weblog/posts/microsoft-exam-70_2d00_535-to-replace-70_2d00_534_3a00_-architecting-microsoft-azure-solutions-on-november-30-_1320_-here_1920_s-what-you-should-know–