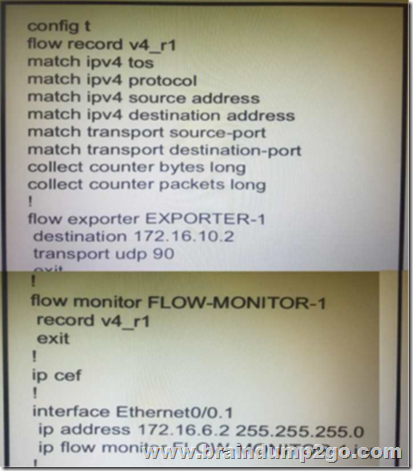
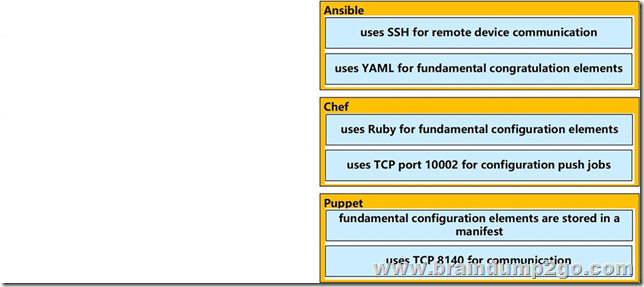
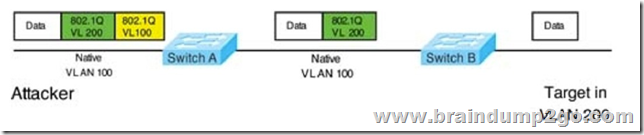
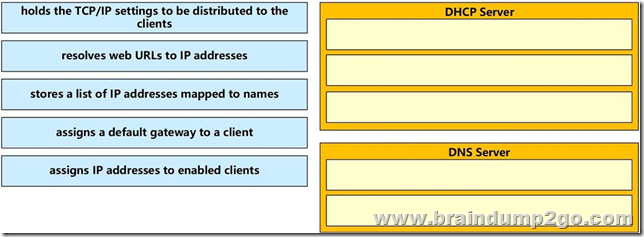
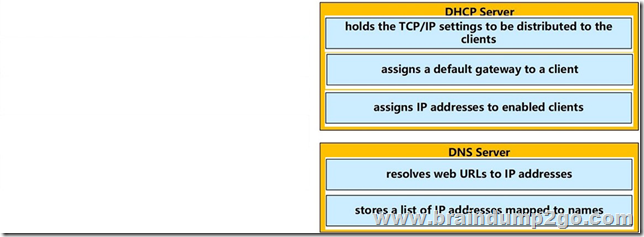
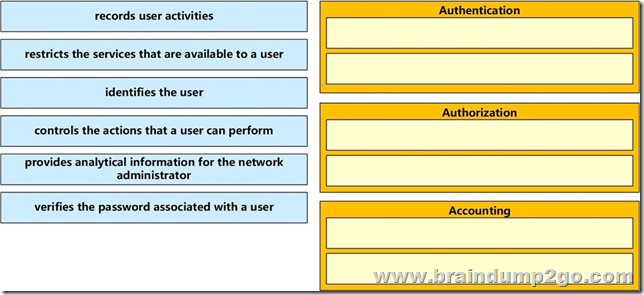
Apr/2020 New Braindump2go MB-600 Exam Dumps with PDF and VCE Free Released Today! Following are some new MB-600 Exam Questions!
QUESTION 13
Note: This question is part of series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
In preparation for a Dynamics 365 Sales and Dynamics 365 Customer Service implementation a client is performing a fit-gap analysis.
You need to evaluate the requirements by using a fit-gap methodology in the context of Dynamics 365 Sales and Dynamics 365 Customer Service. Solution: Users need to update their accounts and add notes while they are offline.
Does the solution meet the goal?
A. Yes
B. No