July/2022 Latest Braindump2go MB-910 Exam Dumps with PDF and VCE Free Updated Today! Following are some new MB-910 Real Exam Questions!
QUESTION 85
A company wants an application that meets the following requirements:
Display the latest news about the company.
Recommend leads to sales team members.
You need to identify an application to meet the requirements. What should you recommend?
A. Dynamics 365 Customer Service
B. Linkedln Campaign Manager
C. Dynamics 365 Sales Insights
D. Linkedln Sales Navigator
Answer: C
QUESTION 86
A company uses Dynamics 365 Sales.
You disqualify a lead. On a later date, the lead shows interest in buying a product that the company sells.
You need to convert the lead to an opportunity and retain all available history.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
A. Qualify the closed lead as an opportunity.
B. Qualify the reactivated lead to an opportunity.
C. Convert the copied lead to an opportunity.
D. Use the Reactivate Lead functionality to reopen the lead.
E. Create a copy of the lead with data from the original lead.
Answer: AB
QUESTION 87
Which three capabilities are included in Dynamics 365 Marketing? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
A. Qualify leads
B. Case management
C. Dynamics 365 Connector for Linkedln
D. Project quote management
E. Event management
Answer: ACE
QUESTION 88
A company uses social media for marketing.
The company wants to use out-of-the-box Dynamics 365 Marketing functionality to streamline social media marketing.
You need to determine the supported social media activities.
Which action is supported?
A. Gel notified when a company is mentioned.
B. Schedule a post to be published in the future.
C. Analyze the sentiment of posts about a company.
D. Automatically follow another account when a specified condition is met
Answer: B
QUESTION 89
A company implements Dynamics 365 Customer Service for their support desk.
Agents resolve issues based on their own personal experiences or they must try to recreate the problem. This is causing customer satisfaction issues as resolution time is longer than expected and not consistent.
You need to implement a solution to improve consistency of answers and ensure that agents can share their answers.
What should you implement?
A. Service level agreements
B. Customer Service Insights
C. Power Automate to transfer cases
D. Knowledge base management
Answer: C
QUESTION 90
A potential customer delays their decision to commit to a big multi-year contract.
You want to find other colleagues who have interacted with the potential customer to discuss strategies.
Which app should you recommend?
A. Customer Service Insights
B. Sales Insights
C. Power Virtual Agents
D. Market Insights
Answer: B
QUESTION 91
You are a consultant working with a company that sells sporting equipment.
The company uses Microsoft 365 and Dynamics 365 Sales.
You need to recommend tools that integrate with Dynamics 365 Sales and improve file collaboration.
What three tools should you recommend? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
A. Power BI
B. SharePoint Online
C. OneDrive for Business
D. Microsoft Teams
E. Power Automate
Answer: BCD
QUESTION 92
A company has a large number of technicians that work in the field.
You need to ensure that Dynamics 365 Field Service can automatically schedule work to minimize travel time for technicians.
What should you implement?
A. Schedule board
B. Unified routing for table records
C. Universal Resource Scheduling
D. Resource scheduling optimization
Answer: D
QUESTION 93
A company is using Dynamics 365 Customer Service for case management.
The company must use entitlements to enforce limitations on customer ticket creation.
You need to design the entitlement terms.
Which two metrics should you use? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
A. Number of hours
B. Number of cases
C. Initial response time
D. Hours of service
Answer: AB
QUESTION 94
A company uses Dynamics 365 Sales with out-of-the-box forms. Users must view logged phone calls and meetings for contacts.
Which feature includes phone calls and meetings?
A. Timeline
B. Contact information
C. Controls
D. Attachments
Answer: A
QUESTION 95
A company uses Dynamics 365 Sales.
The company plans to use Linkedln Sales Navigator to increase sales productivity and assist salespersons in their daily duties.
You need to identify potential decision makers for a sale.
Which Linkedln Sales Navigator feature should you use?
A. Related Leads
B. Top Card
C. Auto Capture
Answer: A
QUESTION 96
A company is working with a potential customer on a multi-year contract. The customer decides to delay their decision to commit to the contract.
You want to find other colleagues who have interacted with the potential customer so that you can discuss strategies with the colleagues to close the deal with the customer.
Which app should you recommend?
A. Power Virtual Agents
B. Sales Insights
C. Customer Service Insights
D. Market Insights
Answer: B
QUESTION 97
A company uses Dynamics 365 Sales. The company creates sales proposals as PDF documents.
The company wants multiple users to access the latest version of a sales proposal in Dynamics 365 Sales. Many users do not have access to Dynamics 365 Sales.
You need to recommend an app for the company.
Which app should you recommend?
A. Dynamics 365 Sales Insights
B. Microsoft Excel
C. Microsoft Outlook
D. Microsoft Teams
Answer: A
QUESTION 98
Sales representatives need a view of all of their customers and the statistics that relate to these customers.
You need to identify how to create visuals for sales representatives to analyze and compare the data for multiple accounts.
What are three possible ways to achieve this goal? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
A. Create custom forms.
B. Embed Power Bl reports in a system dashboard.
C. Create charts.
D. Create reports in the report wizard.
E. Import Excel data.
Answer: BCD
QUESTION 99
A company uses Dynamics 365 Marketing. The company uses a third-party app to send email surveys to prospects to better understand their business needs.
There is currently no link to prospect records and users report that the survey management process is manual and is difficult to manage.
You need to automate the survey process and streamline collection and analysis of responses.
What are two possible ways to achieve this goal? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
A. Use Customer Voice to compile results from the existing third-party app.
B. Use Power Automate to automatically send Customer Voice surveys.
C. Create a survey in Dynamics 365 Marketing and create a campaign to send it to out and collect data.
D. Use Customer Voice to collect and analyze survey results.
E. Create surveys in Dynamics 365 Marketing by using Questionnaire.
Answer: DE
QUESTION 100
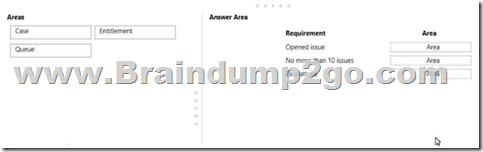
Drag and Drop Question
Dynamics 365 Customer Service has the following requirements:
– Issues created on a website must be added to Dynamics 365 Customer Service.
– A customer must be limited to opening no more than 10 issues a month.
– Escalations must be organized into an area that ensures managers can view escalated issues.
You need to identify the areas in the system that meet the requirements.
Which area should you identify? To answer, drag the appropriate areas to the correct requirements. Each area may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Answer:

QUESTION 101
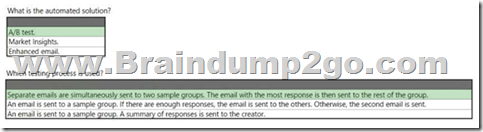
Hotspot Question
A company uses Dynamics 365 Marketing. The company wants an automated solution to test two email designs before launching the entire email campaign.
You need to recommend a solution for the company.
What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
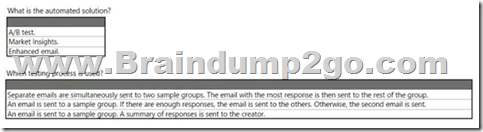
Answer:
QUESTION 102
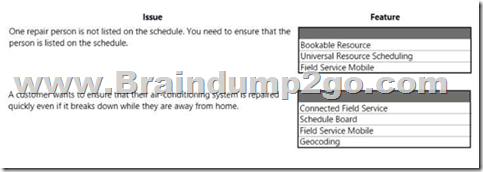
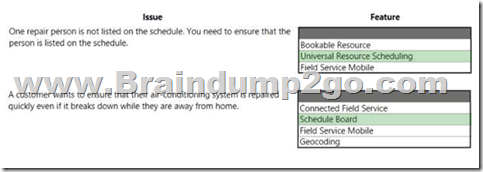
Hotspot Question
An air-conditioning repair company uses Dynamics 365 Field Service, Customers and users report several issues.
What should you use to resolve each issue? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Answer:
QUESTION 103
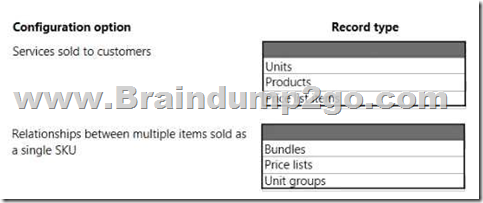
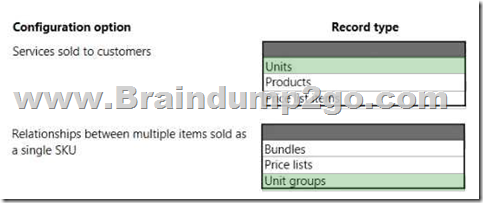
Hotspot Question
A company uses Dynamics 365 Sales.
The sales process must use products.
You need to create the product catalog record type.
Which record types should you create? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Answer:
QUESTION 104
Drag and Drop Question
You use Dynamics 365 Customer Service.
You plan to configure service-level agreements (SLAs) for cases.
Which feature should you use? To answer, drag the appropriate features to the correct scenarios. Each feature may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.

Answer:

QUESTION 105
Drag and Drop Question
A company plans to implement Dynamics 365 Customer Service.
Dynamics 365 Customer Service uses terminology that is different than what the existing customer service solution uses.
You need to create a glossary for employees.
Match each item to its definition. To answer, drag the appropriate definition from the column on the left to its item on the right. Each item may be used once, more than once, or not at all. Each correct match is worth one point.

Answer: 
Resources From:
1.2022 Latest Braindump2go MB-910 Exam Dumps (PDF & VCE) Free Share:
https://www.braindump2go.com/mb-910.html
2.2022 Latest Braindump2go MB-910 PDF and MB-910 VCE Dumps Free Share:
https://drive.google.com/drive/folders/1aF0S_GOE2Vj4YoOM_9pT8lHgdK7Y3hBI?usp=sharing
3.2021 Free Braindump2go MB-910 Exam Questions Download:
https://www.braindump2go.com/free-online-pdf/MB-910-PDF-Dumps(85-105).pdf
Free Resources from Braindump2go,We Devoted to Helping You 100% Pass All Exams!