January/2022 Latest Braindump2go 350-501 Exam Dumps with PDF and VCE Free Updated Today! Following are some new updated 350-501 Real Exam Questions!
QUESTION 172
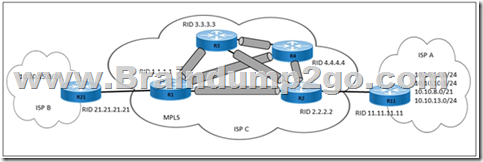
What are two characteristics of MPLS TE turrets? (Choose two)
A. They require EIGRP to be running in the core.
B. They use RSVP to provide bandwidth for the tunnel.
C. They are run over Ethernet cores only.
D. The headend and tailend routes of the tunnel must have a BGP relationship.
E. They are unidirectional.
Answer: BE